Cyber Security Outsourcing
Strengthen Your Defenses with Expert Protection
In today’s rapidly evolving digital landscape, the importance of robust cyber security measures cannot be overstated. Cyber threats continue to grow in sophistication and frequency, posing significant risks to businesses of all sizes. As organizations strive to protect their valuable assets and sensitive data, many are turning to cyber security outsourcing as a strategic solution. By partnering with experienced and specialized professionals, businesses can enhance their security posture, mitigate risks, and focus on their core competencies with peace of mind.
Why Cyber Security Outsourcing?
Expertise and Experience:
Cyber security outsourcing provides access to a pool of seasoned professionals with extensive knowledge and expertise in the field. These professionals possess a deep understanding of the evolving threat landscape, emerging technologies, and best practices for mitigating risks. By leveraging their expertise, businesses can implement robust security measures tailored to their unique requirements, while staying ahead of the ever-changing threat landscape.
Cost Efficiency:
Establishing an in-house cyber security team can be an expensive undertaking. It involves significant investments in hiring, training, infrastructure, and ongoing maintenance. Cyber security outsourcing allows organizations to leverage external resources without the associated costs. By partnering with a reputable service provider, businesses can access cutting-edge technologies, tools, and talent at a fraction of the cost, ultimately reducing their overall expenditure.
24/7 Monitoring and Incident Response:
Cyber attacks can occur at any time, and timely detection and response are crucial for minimizing the impact of such incidents. Cyber security outsourcing offers round-the-clock monitoring, threat intelligence, and incident response services. Dedicated security teams work tirelessly to identify, analyze, and neutralize threats before they can cause significant damage. This proactive approach ensures swift action, minimizing potential downtime, data breaches, and reputational damage.
Scalability and Flexibility:
Businesses often face fluctuations in their cyber security requirements, particularly during peak periods or when launching new initiatives. Cyber security outsourcing provides scalability and flexibility, allowing organizations to easily adjust their resources based on their changing needs. Service providers can quickly scale up or down the level of protection and support, ensuring that businesses have the right level of security at all times.
Compliance and Regulatory Adherence:
Compliance with industry-specific regulations and data protection standards is a critical aspect of modern business operations. Cyber security outsourcing helps organizations navigate complex compliance requirements effectively. Service providers are well-versed in regulatory frameworks, ensuring that security measures align with relevant standards and guidelines. This enables businesses to demonstrate their commitment to data privacy and security, bolstering customer trust and avoiding potential penalties.
As cyber threats continue to evolve, businesses must prioritize cyber security to safeguard their operations, reputation, and customer trust. Cyber security outsourcing offers a strategic approach to counter these threats effectively. By partnering with experienced professionals, organizations can access advanced technologies, industry best practices, and round-the-clock support, bolstering their defenses and ensuring proactive threat mitigation. Embracing cyber security outsourcing empowers businesses to focus on their core objectives while knowing that their digital assets are in capable hands.
XBlock Outsourcing offers state of the art offshore IT support and development services. Our team specializes in Enterprise Solutions & Architecture Consultancy, Database Management, Cyber Security and Digital Transformations.
Essential Controls: 10 Priority areas For Increased Cyber Resilience
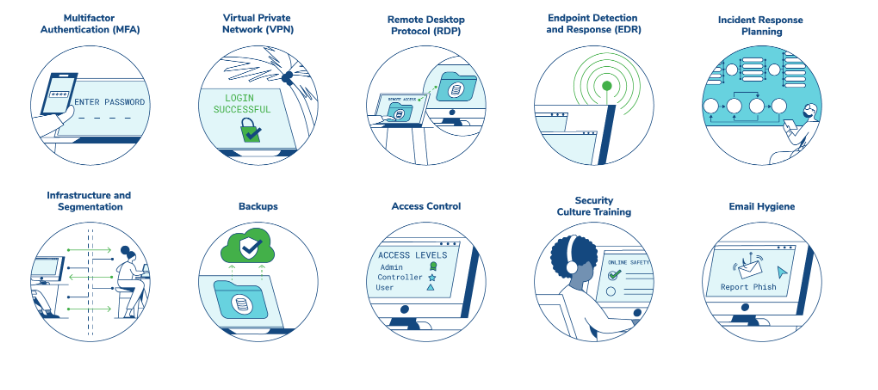
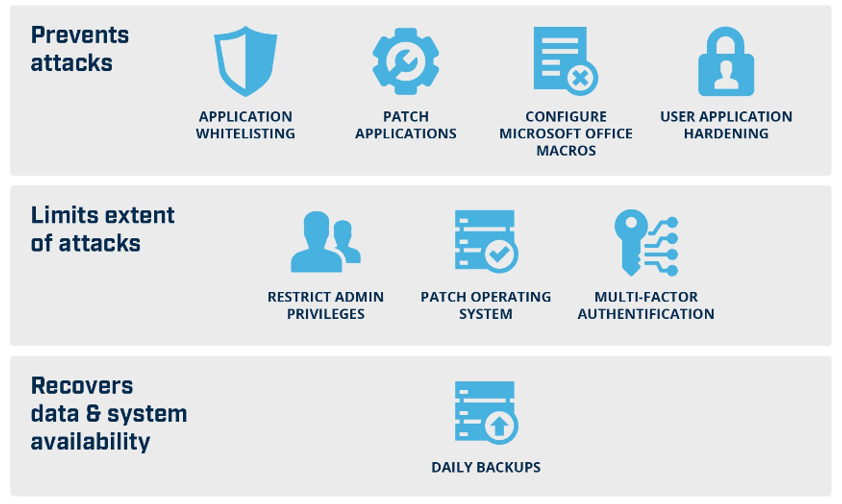
Essential 8 Security Controls
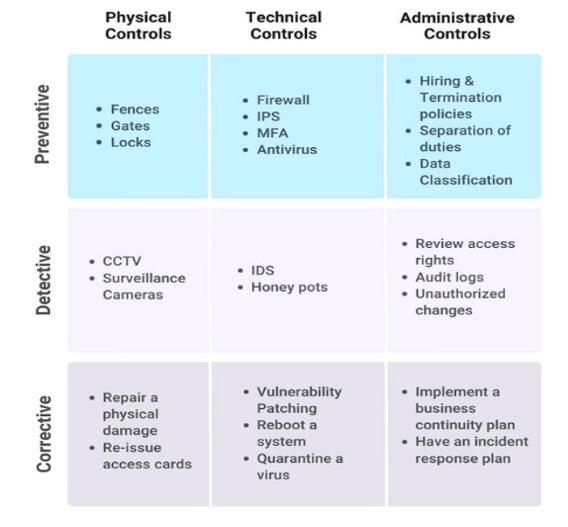
Types Of Cyber Security Controls